In today’s digital age, protecting sensitive information is critical. Be it personal details, business information, or financial data – protecting them from being disclosed to unauthorized parties is important. Common document formats for sharing documents include PDF, but PDFs should be secured when they contain sensitive text. This article explores the methods and best practices for removing sensitive text from PDFs for data security.
Why You Should Secure PDFs
Often used are PDFs (Portable document Format files), which preserve document formatting across devices and platforms. This file format can be a security risk though if not handled correctly. Social security numbers, financial records, or secret business strategies can all be easily extracted if the PDF is not properly secured.
Securing PDFs isn’t just about protecting personal privacy – it’s about complying with data protection laws like GDPR, HIPAA etc. Not securing sensitive information can cause legal issues, financial loss, and damage to reputation.
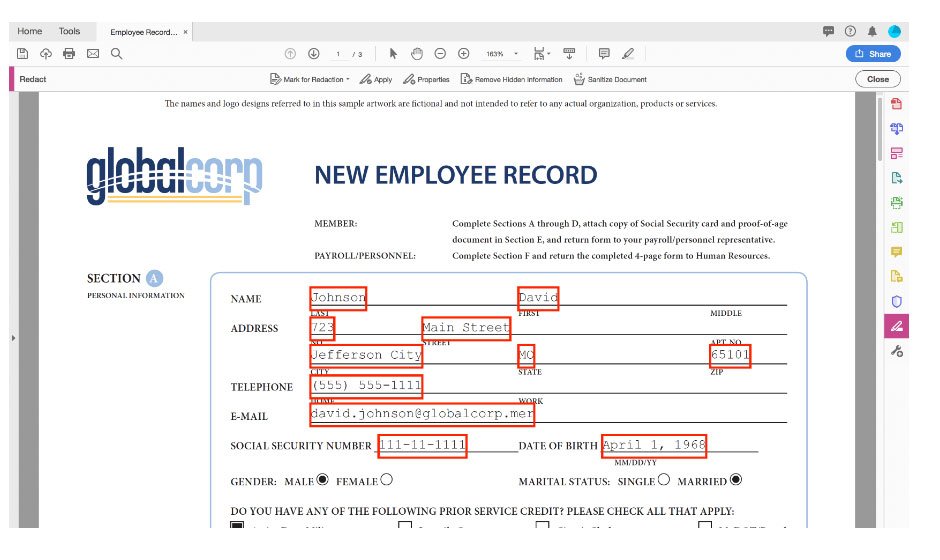
Methods to Remove Sensitive Text from PDFs
The removal of sensitive text from PDFs can take several forms – simple or more advanced. Listed below are some of the best ways to do this:
1. Redaction
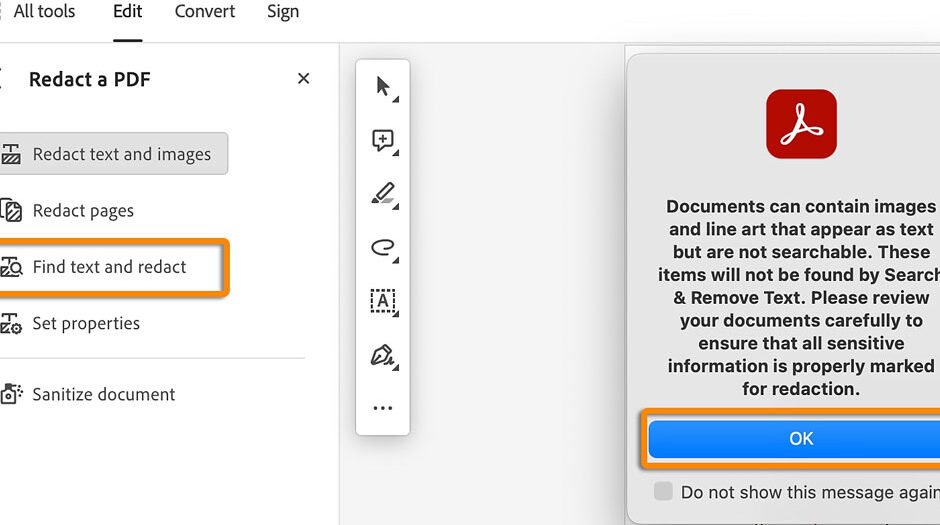
Redaction removes sensitive text or images permanently from a document. This is a safeguard often used in legal documents. Redaction tools cover the sensitive text with a black bar or other symbol and make the original content unrecoverable. Several PDF editing tools such as Adobe Acrobat provide tools for redaction, allowing users to select and redact text easily.
2. Content Removal
Content removal involves physically deleting the sensitive text from the PDF. This works well if the information is no longer needed in the document. But users should be careful that the information is removed and not just hidden. Some PDF editors let users delete specific text or image so the sensitive information is no longer available.
3. Flattening PDFs
Flattening a PDF means combining all the layers into one layer. This is useful for PDFs with forms or annotations. Flattening converts all interactive elements like text fields and annotations to static content. This can prevent the extraction of sensitive information from form fields or comments.
4. Encryption
Encryption does not erase sensitive text but restricts access to the document. Encrypting a PDF lets users set passwords and permissions on who can view, print or edit the document. This is useful when you share PDFs with outside parties as it only allows authorized people to see the private information.
5. Optical Character Recognition OCR Scrubbing
For scanned documents or images converted to PDFs, OCR technology can identify and remove sensitive text. OCR scrubbing tools scan the document for text and users can redact or remove identified sensitive information. This is especially useful for handling sensitive scanned documents.
Best Practices for Removing Sensitive Text Securely
Removing sensitive text from PDFs should follow best practices to protect the information.
Double-Check Redactions: Once you redact sensitive information, always check the document again to make sure all sensitive text has been removed.
Use Trusted Software: Only remove sensitive information using trusted and reputable PDF editing software. Those free or unverified tools may lack adequate security features.
Test the Document: After removing sensitive information, test the document by copying, searching or extracting the redacted text.
Save a Copy: Save a copy of the original document before making edits. This precaution lets you revert to the original if needed.
Secure the Final Document: After removing sensitive text, you can encrypt the PDF or grant permissions to protect it further.
Conclusion
Removing sensitive text from PDFs is one way to secure personal and business information. Redaction, content removal, flattening and encryption are some of the most effective ways that individuals and organizations can prevent unauthorized access to their data.